Breaking News




Popular News













Enter your email address below and subscribe to our newsletter
Google Cloud network architecture explained, focusing on VPC design, scalability, security boundaries, and real-world patterns for production environments.
Google Cloud network architecture forms the foundation of every secure, scalable, and high-performance cloud environment. Although teams often focus first on compute sizing or storage choices, the network layer ultimately determines how workloads communicate, how systems scale across regions, and how effectively security boundaries are enforced. In practice, network design decisions tend to outlive most other architectural choices, which makes them especially critical early in any cloud journey.
This article examines Google Cloud networking from an architectural perspective. Rather than listing individual services, it explains how core design decisions—around Virtual Private Cloud (VPC) structure, subnet segmentation, hybrid connectivity, traffic flow, and security controls—directly influence reliability, operational risk, and long-term cost. The emphasis is therefore on why certain patterns work, not merely how to configure them.
Any effective cloud network design begins with a clear understanding of responsibility boundaries. Google Cloud owns and operates the physical layer, including global fiber infrastructure, data centers, hardware, and the backbone network that interconnects regions and zones worldwide. As a result, customers never manage switches, routers, or physical links.
However, customers fully control the virtual layer. Architects design VPC networks, define IP address ranges, segment workloads into subnets, configure routing behavior, and enforce firewall policies. They also decide how environments connect to on-premises systems or external networks using managed connectivity services. Consequently, while the physical network remains abstracted, architectural responsibility does not disappear—it simply moves up the stack.
This distinction matters because the virtual network defines security boundaries, failure domains, and scaling limits. When teams underestimate the importance of these decisions, they often create flat networks that seem convenient initially but become fragile at scale. Over time, correcting those early choices becomes increasingly expensive and disruptive.
Network architecture directly shapes business outcomes because it influences scalability, security, performance, and cost simultaneously. A well-designed network allows applications to scale horizontally without redesign, isolates sensitive components to reduce blast radius, and delivers predictable latency across regions. As a result, engineering teams can focus on product development rather than constant infrastructure remediation.
In contrast, poorly structured networks tend to accumulate hidden risk. Flat subnet layouts force broad firewall rules, which weaken security controls. Limited segmentation increases the impact of failures. Furthermore, inefficient traffic routing raises latency and inflates data transfer costs. These issues rarely appear during early testing, yet they surface quickly once real users and production traffic arrive.
Moreover, no single network design fits every organization. Architectures that work well for stateless web applications may fail in regulated industries or latency-sensitive platforms. Therefore, effective Google Cloud network architecture must reflect application behavior, compliance requirements, user geography, and expected growth. Treating network design as a one-time configuration exercise almost always leads to technical debt.
Before deploying any networking components, architects must invest time in structured planning. This phase determines which services to use, how to combine them, and where trade-offs between performance, security, and cost are acceptable.
Planning begins with a realistic assessment of current and future needs. Teams should evaluate user volumes, application types, traffic patterns, data sensitivity, and integration requirements with on-premises or third-party systems. At the same time, they must anticipate growth, including new regions, higher availability targets, or stricter regulatory constraints.
From this assessment, architects should define measurable objectives. Latency targets, availability goals, security constraints, and cost ceilings provide concrete benchmarks for evaluating design decisions. Consequently, teams avoid reactive changes later and preserve architectural consistency as the environment evolves.
Google Cloud offers a comprehensive networking portfolio that supports everything from small single-region deployments to globally distributed hybrid architectures. However, strong designs emerge only when architects select and combine services deliberately rather than adding components in response to isolated problems.
The Virtual Private Cloud (VPC) sits at the center of every Google Cloud network design. A VPC defines an isolated virtual network in which resources communicate using private IP addressing. Through subnet design, architects segment workloads by function, security level, or lifecycle stage.
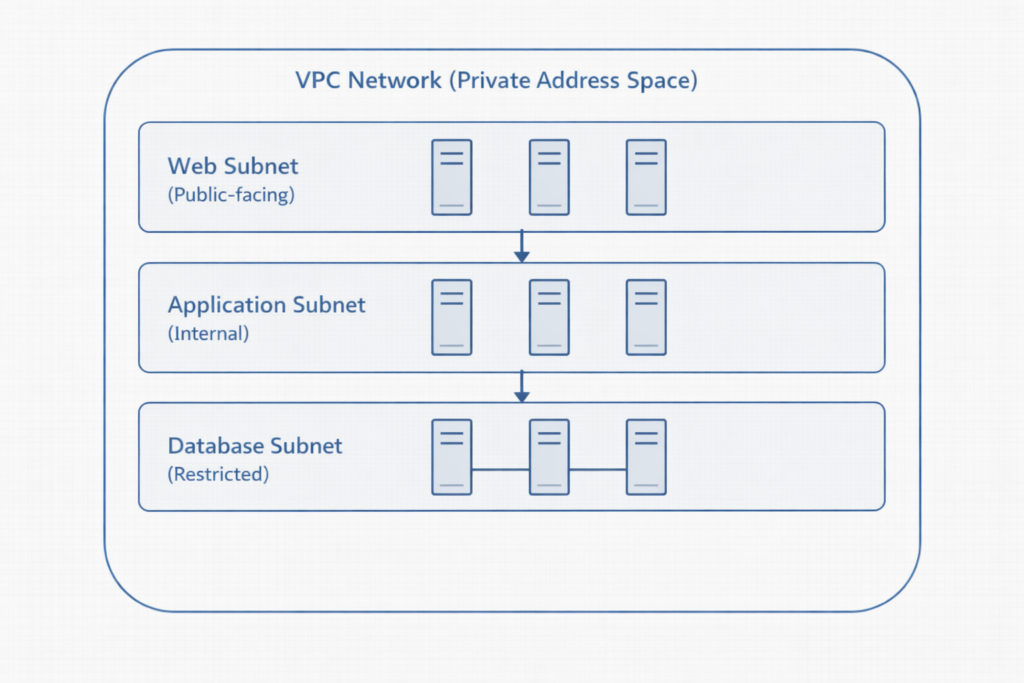
Too often, teams treat a VPC as a simple container. As a result, they deploy all workloads into a small number of subnets, which forces overly permissive firewall rules and complicates isolation later. In contrast, thoughtful subnet segmentation from the outset simplifies security enforcement, reduces blast radius, and improves operational clarity as environments grow.
For many organizations, cloud adoption extends existing on-premises environments rather than replacing them. Google Cloud supports this hybrid reality through multiple connectivity options.
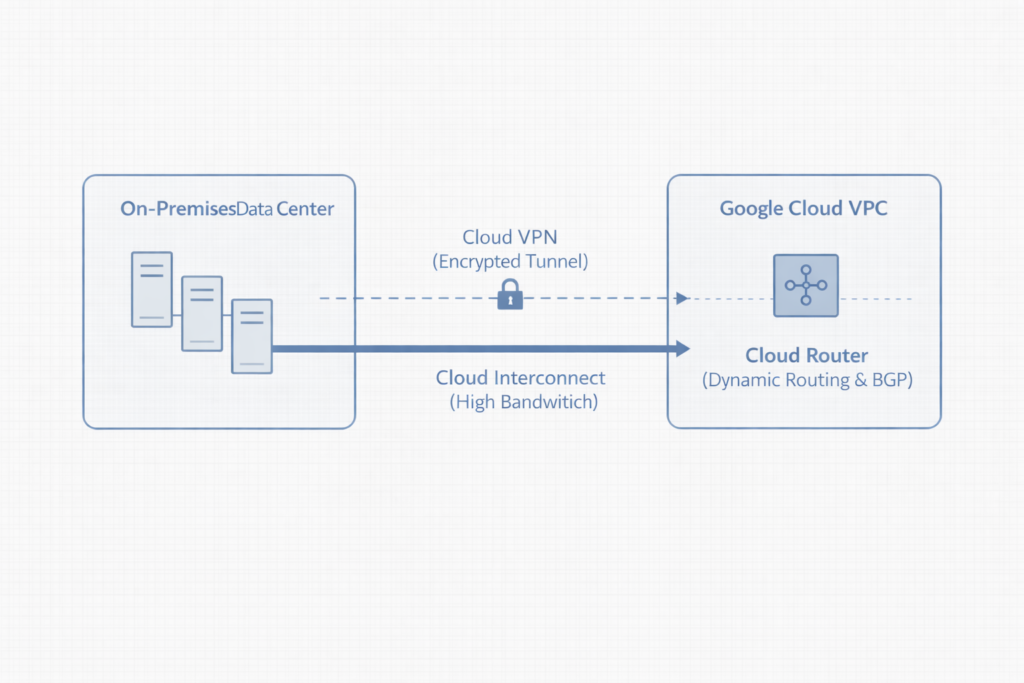
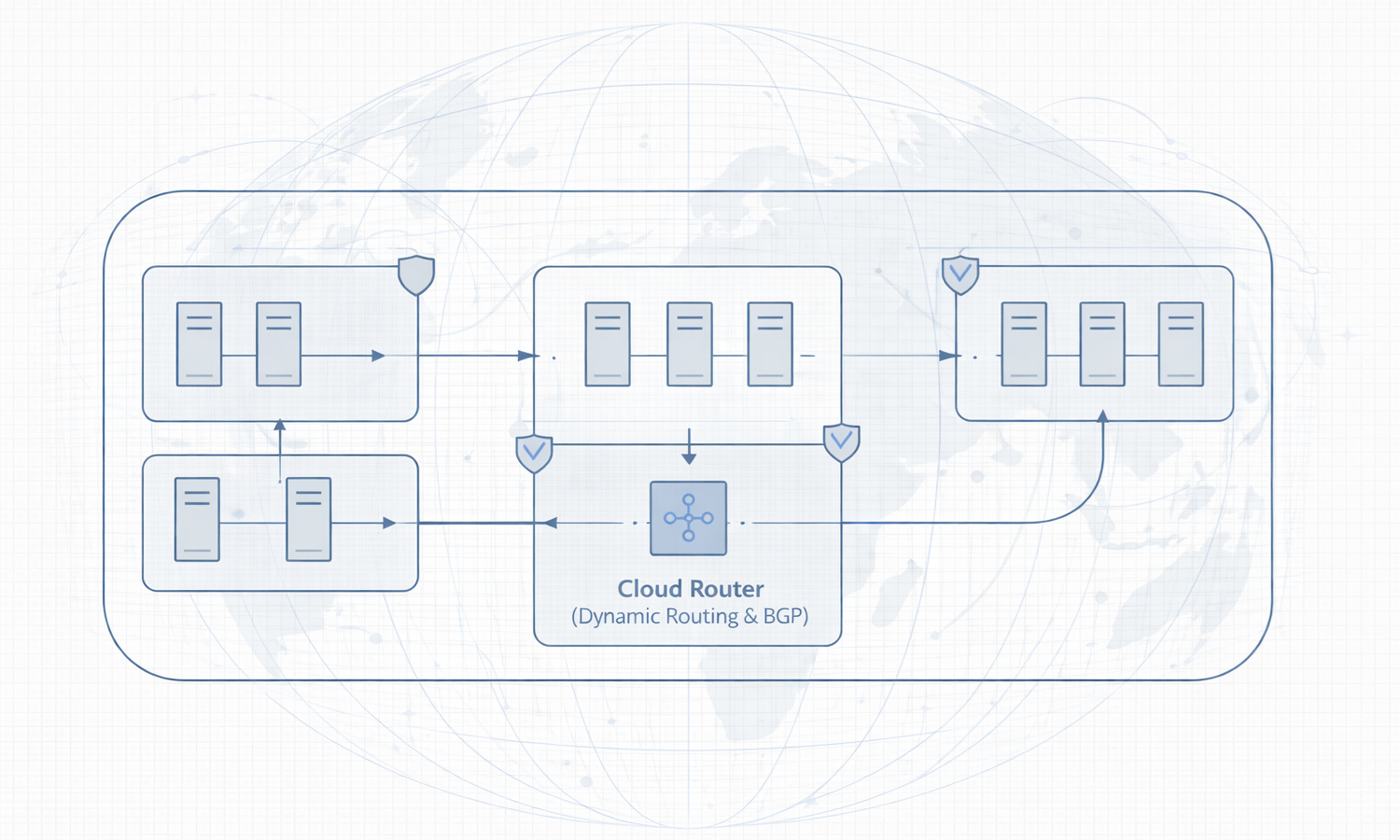
Cloud VPN enables encrypted tunnels over the public internet and works well for moderate throughput or rapid initial connectivity. Meanwhile, Cloud Interconnect provides dedicated, high-bandwidth, low-latency connections for demanding workloads. In advanced designs, teams can combine these options by layering VPN over Interconnect to achieve both encryption and performance.
Cloud Router plays a central role by dynamically exchanging routes using Border Gateway Protocol (BGP). Additionally, it supports services such as Cloud NAT, which enables scalable outbound connectivity without exposing internal resources. As a result, routing behavior remains predictable even as environments expand.
As applications scale, controlling how users reach backend services becomes critical. Google Cloud load balancers distribute traffic across instances and regions, thereby preventing overload and improving availability. Because these load balancers operate at multiple layers, architects can optimize traffic handling for HTTP(S), TCP, or UDP workloads.
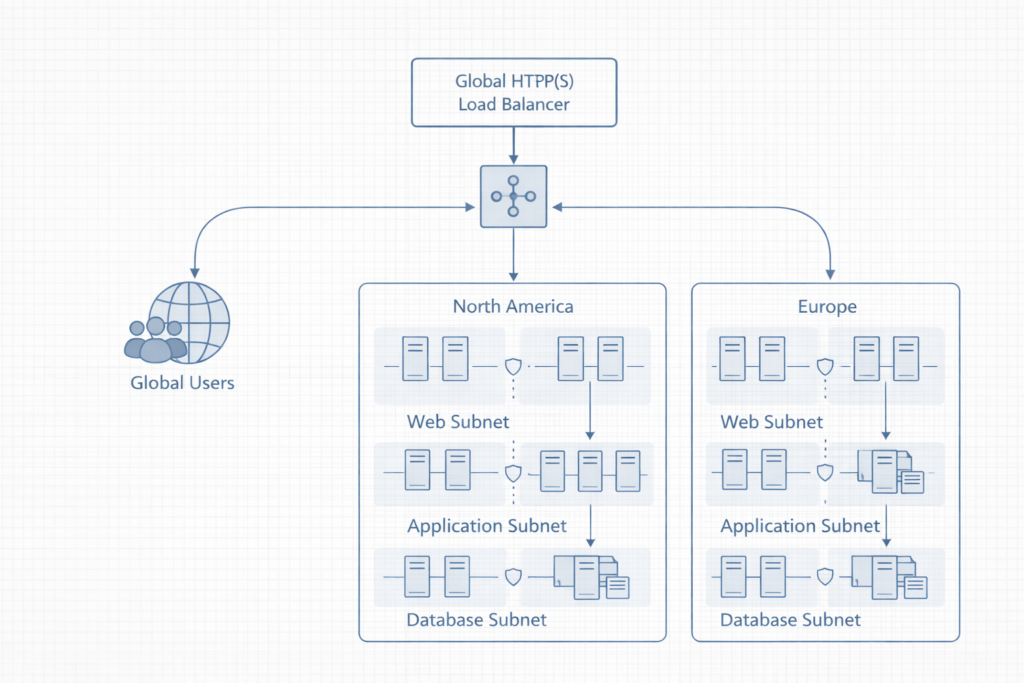
Furthermore, Cloud CDN improves global performance by caching content closer to users, reducing latency and backend load. Network Service Tiers allow teams to balance performance and cost by choosing between premium global routing and standard regional paths. Consequently, architects can align network behavior with application requirements instead of defaulting to over-provisioned designs.
Network security relies primarily on firewall rules and policies that explicitly define allowed traffic flows. These controls apply at fine granularity and can be centrally managed through firewall policies, which simplifies operations at scale.
At the same time, architects must clearly separate network controls from identity controls. Firewalls regulate packet flow, whereas IAM governs who can manage resources. Effective architectures combine both layers so that access remains constrained by network boundaries and user identity.
A mid-sized financial services provider operates a customer portal that supports transactions, reporting, and account management. Initially, the organization designed the platform for a regional audience and deployed it within a single Google Cloud VPC.
The original design placed the web front end, application services, and database inside one subnet. Although this approach simplified deployment, it also introduced structural limitations. All components shared the same security context, traffic flowed without load balancing, and availability depended on a small number of virtual machines in one region.
As the organization expanded into additional European and North American markets, these weaknesses became increasingly visible. Security teams struggled to isolate sensitive data stores, scaling required manual intervention, and traffic spikes increased the risk of degraded performance. Most importantly, the lack of redundancy created single points of failure.
To address these issues, the team redesigned the platform around subnet-based segmentation and distributed traffic management. Each application tier moved into its own subnet, with firewall rules applied independently. Public access terminated at the web tier, while internal tiers remained isolated. In addition, an external load balancer distributed traffic across multiple backend instances and regions.
This redesigned Google Cloud network architecture enabled horizontal scaling, reduced operational risk, and delivered predictable performance for global users without sacrificing security.
Google Cloud network architecture enables reliable, scalable cloud systems when teams treat it as a strategic discipline rather than a configuration task. By understanding how VPCs, routing services, load balancers, and security controls interact, architects can design environments that scale predictably, remain secure under pressure, and adapt to changing business needs.
Ultimately, organizations that invest early in thoughtful network architecture build cloud foundations that support both current workloads and future growth—without costly redesigns later.