Breaking News


Popular News












Enter your email address below and subscribe to our newsletter

Microsoft Entra identity management forms the foundation of modern cloud security. In today’s cloud-first and hybrid environments, identity has effectively replaced the traditional network perimeter as the primary line of defense. Instead of relying on isolated internal networks, organizations now depend on identity-driven controls to determine who can access resources, from where, and under which conditions.
As a result, organizations must design identity strategies that clearly define how users authenticate, how access decisions are evaluated, and how resources remain protected across cloud and hybrid platforms. This shift reflects broader industry trends toward zero-trust security models, where no user or device is implicitly trusted.
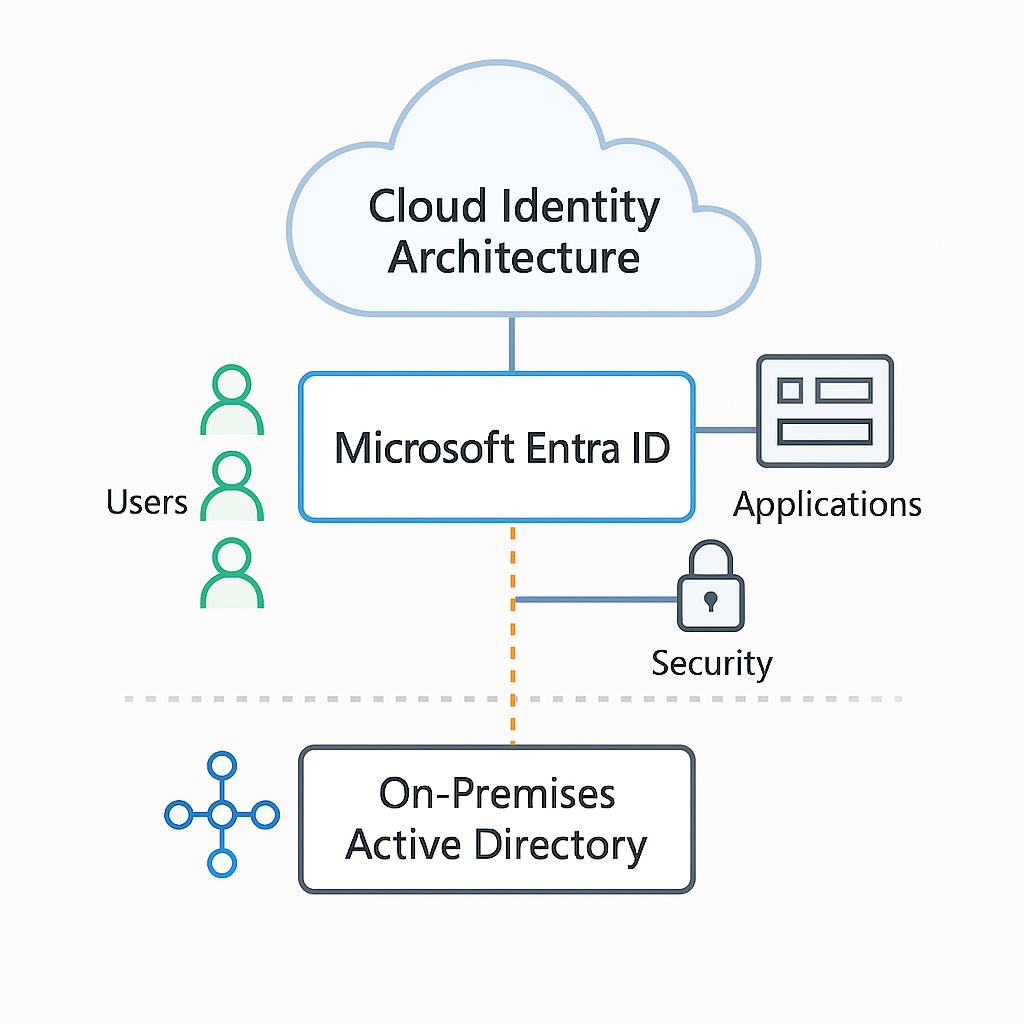
Recently, Microsoft introduced a significant branding change in this space. Azure Active Directory (Azure AD) is now known as Microsoft Entra ID. Although Azure AD remains a familiar term across documentation, training material, and existing implementations, Microsoft now positions Entra ID as part of a broader, security-focused identity portfolio. Therefore, when you encounter Azure AD references, you should interpret them as Microsoft Entra ID.
For many years, Azure Active Directory served as Microsoft’s primary cloud identity platform. Organizations relied on it to authenticate users, manage groups, and secure access to Microsoft 365, Azure resources, and SaaS applications. Over time, however, enterprise requirements evolved. Organizations began adopting zero-trust architectures, large-scale SaaS ecosystems, and hybrid cloud models.
Consequently, Microsoft expanded its identity capabilities to address governance, external identities, and advanced access controls. To reflect this broader scope, Microsoft unified these capabilities under the Microsoft Entra brand.
The key point remains clear:
Microsoft did not replace Azure Active Directory; instead, it rebranded it as Microsoft Entra ID.
This rebranding highlights Microsoft’s strategic focus on cloud-native identity, centralized governance, and consistent security controls across both Microsoft and third-party platforms. Importantly, the underlying service continues to evolve without disrupting existing deployments.
IdeIdentity management defines how organizations issue, protect, and govern digital identities throughout their lifecycle. In practical terms, Microsoft Entra identity management includes:
Within Microsoft Azure, Microsoft Entra ID provides these capabilities as a native service. As a result, architects and administrators use Entra ID as a foundational security layer when designing cloud solutions. Rather than embedding authentication logic into each application, teams centralize identity decisions within Entra ID, which simplifies management and improves security consistency.
It is essential to distinguish Microsoft Entra ID from Microsoft Active Directory.
Microsoft Active Directory operates entirely on-premises. It manages users, groups, computers, and network objects within local infrastructure and depends on internal network connectivity. Organizations traditionally use it to secure Windows-based environments, file servers, and line-of-business applications.
Microsoft Entra ID, by contrast, operates as a cloud-native identity platform. It supports internet-facing applications and integrates directly with cloud services. Although the two platforms share conceptual similarities, they do not replace one another. Instead, most organizations deploy hybrid identity architectures, where Entra ID extends on-premises Active Directory into the cloud using synchronization and federation technologies.
This hybrid approach allows organizations to modernize authentication while preserving existing investments in on-premises infrastructure.
Traditional Active Directory environments rely on protocols such as Kerberos and LDAP. However, these prTraditional Active Directory environments rely on protocols such as Kerberos and LDAP. While these protocols work well within controlled internal networks, they do not function effectively over the public internet. Therefore, cloud identity platforms require modern, web-compatible standards.
Microsoft Entra ID uses protocols such as:
These standards enable secure authentication and authorization over HTTP and HTTPS. Consequently, Entra ID integrates seamlessly with web applications, APIs, and SaaS platforms, regardless of where users or applications are located.
Microsoft Entra ID functions as a centralized identity provider for both Microsoft and non-Microsoft Microsoft Entra ID functions as a centralized identity provider for both Microsoft and non-Microsoft applications. For example, organizations can integrate:
By using Entra ID as a common authentication authority, organizations apply consistent authentication rules, enforce access policies, and manage permissions from a single identity control plane. As a result, administrators reduce operational complexity while improving security visibility and compliance.
Microsoft Entra represents a broad identity and access management ecosystem. In addition to basic authentication, it includes conditional access, identity governance, external identities, and access lifecycle management. Because of this breadth, a single article cannot cover every capability in detail.
Instead, this post establishes a foundational understanding of how Microsoft Entra supports identity and access management in cloud and hybrid environments. Subsequent topics can build on these concepts by exploring advanced configuration, real-world scenarios, and architectural best practices.
For detailed and authoritative documentation, Microsoft provides an official overview of the Entra platform:
https://www.microsoft.com/en-us/security/business/microsoft-entra
Microsoft Entra ID plays a critical role in modern cloud security architectures. It enables organizations to manage identities, control access, and secure applications across cloud and hybrid environments. As cloud adoption accelerates and security threats evolve, identity-driven controls become increasingly important.
Professionals who understand Microsoft Entra identity management gain a significant advantage in designing secure, scalable, and future-ready solutions. Future articles can explore advanced topics such as conditional access policies, identity governance, and hybrid identity synchronization in greater depth.